Author/Source: The Hacker News See the full link here
Takeaway
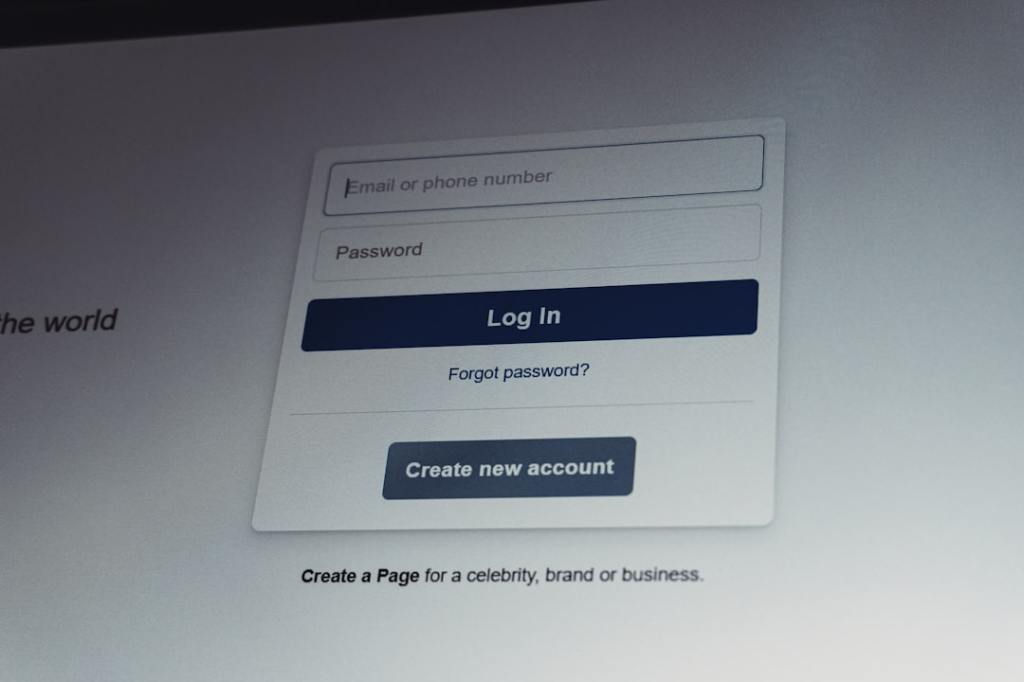
This article explains a new hacking tool called Matrix C2 that tricks people into giving away their login information. It does this by creating fake login screens that appear within your web browser but are not real. You will learn how this tool works and why it is a threat to your online security.
Technical Subject Understandability
Intermediate
Analogy/Comparison
This attack is like a thief putting a very realistic fake door in front of your real door. When you try to open the fake door with your keys, you actually give the thief your keys without realizing it.
Why It Matters
This type of attack is dangerous because it can steal your passwords and even bypass extra security steps like two-factor authentication. For example, if you click a bad link, this attack could trick you into typing your bank login details into a fake window, giving hackers access to your money.
Related Terms
Phishing, Credential harvesting, Browser-in-browser, Multi-factor authentication (MFA). Jargon Conversion: Phishing is a trick hackers use to get your private information by pretending to be a trustworthy source. Credential harvesting is when hackers collect your usernames and passwords. Browser-in-browser is a hacking technique where a fake browser window appears inside your real browser to trick you. Multi-factor authentication (MFA) is an extra security step, usually needing a second way to prove who you are besides your password.

Leave a comment